The configuration in this blog is to set Azure AD authentication for authenticating Business Central users.
Important:
Azure AD authentication with WS-Federation has been deprecated in later Business Central releases and replaced with OpenID Connect. For more information, see Moving from WS-Federation to OpenID Connect. But if you’re running Business Central 2022 release wave 1 (version), you have the option to WS-Federation.
Prerequisites
- Azure AD Tenant
- Business Central Application
Firstly, we need to gather some Key Information while Azure App Registration listed below:
Primary domain: Domain.com
Application (client) ID: xxxxxxxxxxxxxxx
Directory (tenant) ID: xxxxxxxxxxxxxxxxx (Tenant ID)
Application ID URI: api://xxxxxxxxxxxxxxxxx
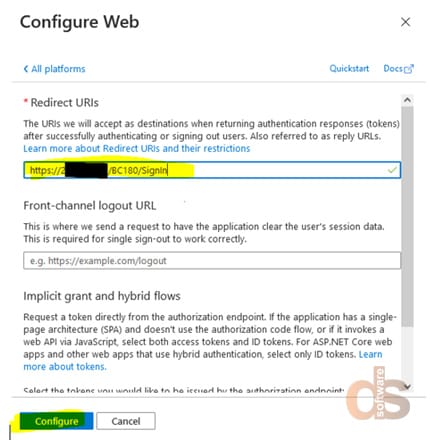
Redirect URIs: https://<IP Address>/<Business Central Instance>/SignIn
1. Azure APP registration
Step1: Sign into Azure Portal
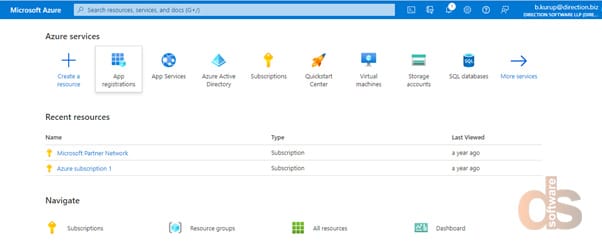
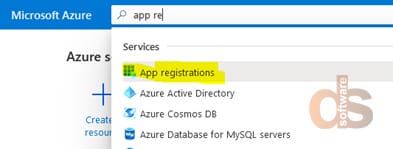
Step 2: Search for App Registration
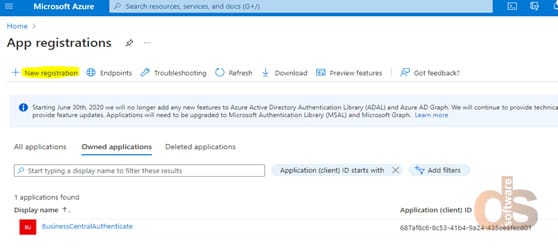
Step 3: Choose New Registration
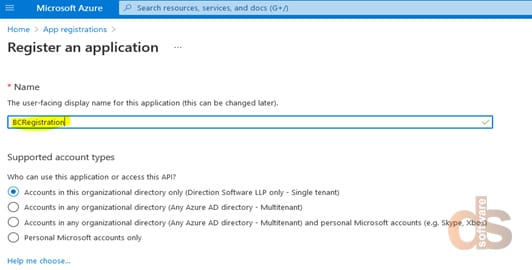
Step 4: Register BC application, enter a Name and click “Register” button
Step 5: Get a screen similar to the below, and click the link “Add an Application ID URI”
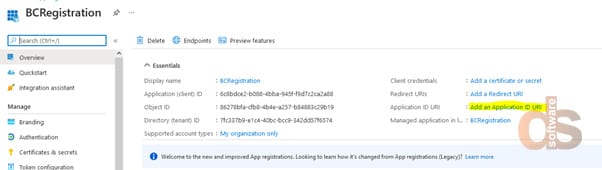
Step 6: Add a scope
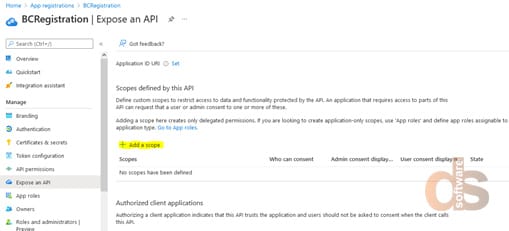
Step 7: Click “Save and Continue”
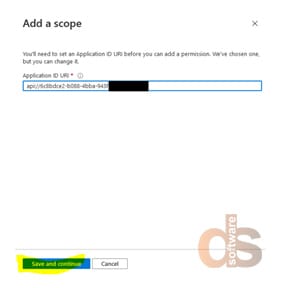
Step 8: Click “Cancel”
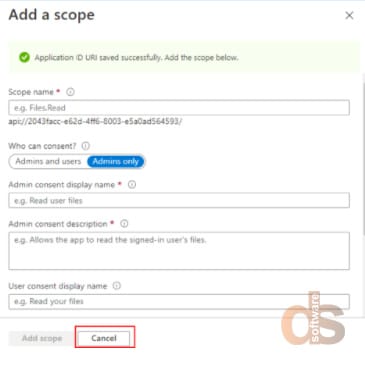
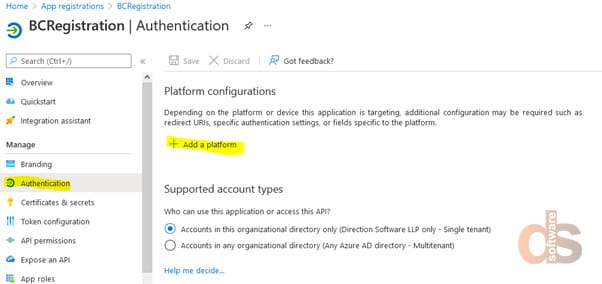
Step 9: Authentication
Step 10: Configure Web
Important:
We need to grant “Sign in and read user profile” permission to all the users to Authenticate Multifactor Authentication.
2. Associate Azure AD Users with Business Central Users
- Start the Business Central, and open the Users page.
- Open the user that you want to modify.
- Under Microsoft 365 (Authentication), set the Authentication Email to the user principle name in Azure AD.
3. Configure Business Central Serve
- Open the Business Central Server Administration tool.
- In the General tab, set the Credential Type to AccessControlService.
- Configure the Azure Active Directory settings.
In the below steps add the details which we collected while Azure APP Registration.
a. Set the WS-Federation Login Endpoint parameter.
The WS-federation login endpoint is the URL of the sign-on page that Business Central redirects to when users sign in from a client. Specify a URL in the following format:
https://login.microsoftonline.com/<AAD TENANT ID>/wsfed?wa=wsignin1.0%26wtrealm=<Application ID URI>%26wreply=<Redirect URL>
Important:
The string parameter must be URI-encoded. This means, for example, use “%26” instead of “&”.
Example
https://login.microsoftonline.com/cronusinternationltd.onmicrosoft.com/wsfed?wa=wsignin1.0%26wtrealm=https://cronusinternationltd.onmicrosoft.com/businesscentral%26wreply=https://cronusinternationltd.onmicrosoft.com/BC190/SignIn
b. Set the WS-Federation Metadata Location parameter.
The WS-federation metadata location establishes a trusting relationship between Business Central and Azure AD. The parameter value has the following format:
https://login.microsoftonline.com/<AAD TENANT ID>/FederationMetadata/2007-06/FederationMetadata.xml
Example
https://login.microsoftonline.com/cronusinternationltd.onmicrosoft.com/FederationMetadata/2007-06/FederationMetadata.xml
4. To configure SOAP and OData web services for Azure AD authentication, specify the App ID URI that is registered for Business Central in the Azure AD.
On the Azure Active Directory tab, set the Azure AD App URI. The App ID URI is typically the same as the wtrealm parameter value of the WS-Federation Endpoint setting.
5. Increase the ExtendedSecurityTokenLifetime parameter value greater than 8 hours.
6. Disable token-signing certificate validation by selecting the Disable Token-Signing Certificate Validation check box.
7. Restart the server instance.
4. Configure Business Central Web Server components
- Open the navsettings.json for the Business Central Web Server in any editor and set the
ClientServicesCredentialTypekey value toAccessControlService. - Save the navsettings.json file and restart the server instance.
About the author:
Kratika Pakhale
Kratika Pakhale is a Microsoft NAV/Dynamics 365 Business Central Technical Consultant working on languages such as CAL and AL at Direction Software LLP.
